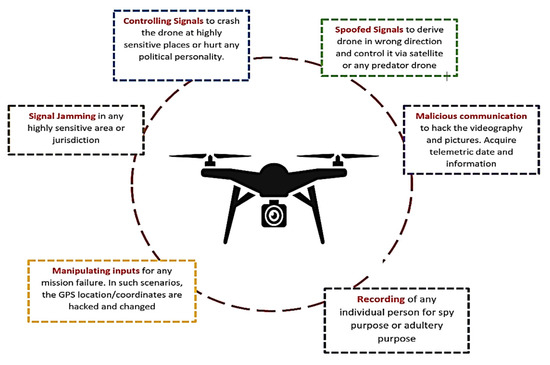
It has been observed that unmanned aerial vehicles (UAVs), also known as drones, have been used in a very different way over time. The advancements in key UAV areas include detection (including radio frequency and radar), classification (including micro, mini, close range, short range, medium range, medium-range endurance, low-altitude deep penetration, low-altitude long endurance, and medium-altitude long endurance), tracking (including lateral tracking, vertical tracking, moving aerial pan with moving target, and moving aerial tilt with moving target), and so forth. Even with all of these improvements and advantages, security and privacy can still be ensured by researching a number of key aspects of an unmanned aerial vehicle, such as through the jamming of the control signals of a UAV and redirecting them for any high-assault activity. This review article will examine the privacy issues related to drone standards and regulations. The manuscript will also provide a comprehensive answer to these limitations. In addition to updated information on current legislation and the many classes that can be used to establish communication between a ground control room and an unmanned aerial vehicle, this article provides a basic overview of unmanned aerial vehicles. After reading this review, readers will understand the shortcomings, the most recent advancements, and the strategies for addressing security issues, assaults, and limitations. The open research areas described in this manuscript can be utilized to create novel methods for strengthening the security and privacy of an unmanned aerial vehicle. View Full-Text ►▼ Show Figures
Figure 2]]>
— — — — — — — — This is an open access article distributed under the Creative Commons Attribution License which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Source



